Access Management for Your Plant and Machinery

For comprehensive protection of your staff and optimum safeguarding of your machinery, you need a holistic safety concept, which considers aspects of both safety and security
With PILZ’s “Identification and Access Management” portfolio, they offer you a comprehensive range of products, solutions and software for the implementation of safety as well as security tasks. Below you’ll discover more about potential applications, from simple authentication to complex access permissions, and access management through to safe operating mode selection, maintenance safeguarding and safeguarding of data and networks. Experience safety and security in one system!
Maintenance safeguarding system “key-in-pocket” for protection against unauthorized restart
This solution ensures that a machine cannot resume operation while people are still in the danger zone. The maintenance safeguarding system “key-in-pocket” is designed for machines with danger zones, which are protected by a safety fence and which staff need to access – robot cells for example. In comparison with conventional lockout-tagout (LOTO) systems, maintenance safeguarding with the key-in-pocket solution is implemented via RFID keys with corresponding permissions and a safe list in the PILZ controllers. As a result, it provides a purely electronic restart protection and makes both mechanical interlocking devices and warning tags redundant.
How this works
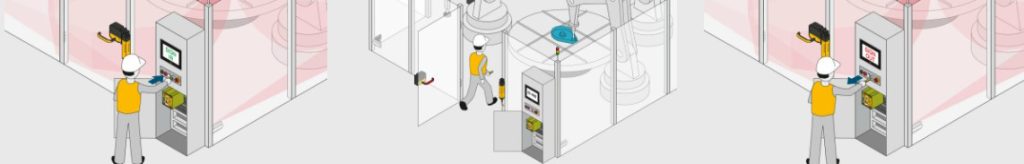
To access the plant, the operator uses their personal transponder key on the PITreader to authenticate themself on the safety gate. The user’s permission is verified and once successfully authenticated, their security ID is stored in a safe list in the PILZ controller (PNOZmulti 2 or PSS 4000).
The machine can now be shut down, the safety gate opened, and the machine accessed. The staff member keeps hold of the transponder (“key-in-pocket”). Additional operators can sign in using their personal key in the same way and thus access the plant. Different safety gates may also be used for access.
For the plant to resume operation, everyone must have exited the plant, closed the safety gates and used their personal key to sign out via the PITreader. The security IDs are removed from the safe list in the controller. Once the list is empty, the machine is enabled. Where plants are large with no overall view, there is an additional “blind spot check” in accordance with EN ISO 13849-1 5.2.2. This requires a visual inspection of the plant in areas that are difficult to see before the machine can be restarted.
Your benefits at a glance
- Authentication of persons, safe restart protection
- Certifications: PL d Cat. 3 of EN ISO 13849-1, SIL CL 2 of EN 62061 and SIL 2 of IEC 61508
- Full control over which person has access to which machine, temporary permission also possible
- Simple to block, plus fast to reprogram when a transponder key is lost
- Considerably cheaper and more flexible as systems are made of metal
- Full traceability of who was in the plant and when (can be deactivated)
- Up to 20 people can access a machine at the same time
- Manual reset function, “blind spot check” in accordance with EN ISO 13849-1 5.2.2.
- Authorized personnel can delete the safe list, “key list reset”
- They do not need to exit the plant via the same door they used to enter
The maintenance safeguarding system “key-in-pocket” consists of the following components:

| Controller | Reader unit | Input device | |
| Type 1 | PNOZ m B1 or PSS4000 | PITreader | Illuminated pushbutton |
| Type 2 | PNOZ m B1 or PSS4000 | PITgatebox with PITreader | PITgatebox with PITreader |
Functionally safe operating mode selection up to PL d Cat 3
Operating mode selection is part of functional safety if it is necessary to switch between different safety levels and safety functions. This is frequently the case if a tool change is pending, or a machine is to be reconfigured. One or more safety devices, such as safety gates or enabling switches for example, can be switched on or off, depending on the selected operating mode. The associated increased risk of damage to the plant and injury risk to personnel must be minimized. To exclude misuse and tampering as much as possible, access to operating mode selection must be restricted to appropriately qualified staff and must be designed to be as convenient and simple for the user as possible.
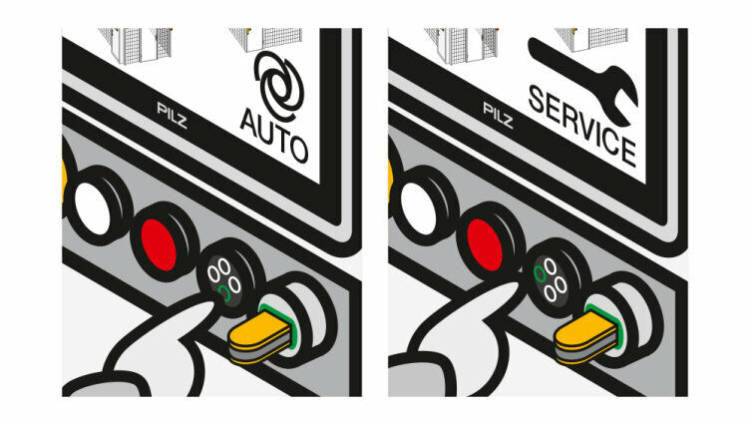
The operating mode and access permission system PITmode not only offers functionally safe switching of the operating mode through self-monitoring up to PL d Cat 3 of EN ISO 13849-1 or SIL CL 2 of EN 62061, but also controls access rights. As such it is the ideal solution for your machinery. With its electronic keys, it provides significantly more security than classic keys. That’s because, all too often, they are inserted in the machine and thus offer just as little security as password protection, as the password is often commonly known.
PITmode fusion can be used with all failsafe controllers. The safe evaluation unit detects the specified operating mode, evaluates it, and provides functionally safe switching. Implementation is even simpler with the small controller PNOZmulti 2 or the automation system PSS 4000, because the safe evaluation unit that reads the operating mode is already available as a function block. The operating mode is selected via a pushbutton (PITmode flex) or via touch input on a PMI panel (PITmode flex visu).
More about the operating mode selection and access permission system PITmode
Access permissions and access management
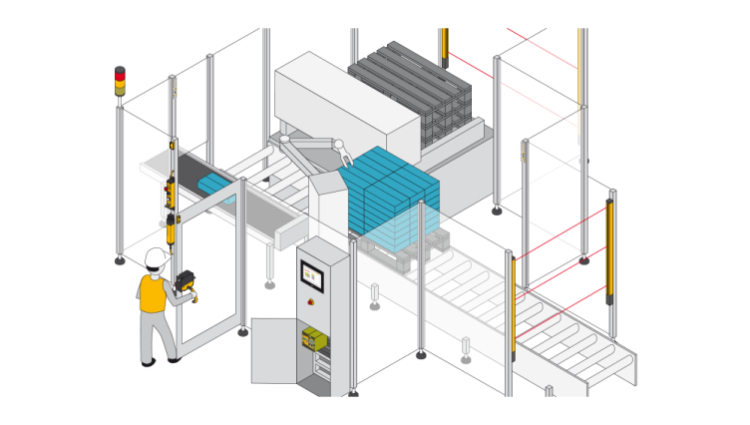
Protect your plant and machinery from access by unauthorized persons! Selective access to hazardous machines, with user authentication, protects your staff from injury and your machines from improper use and damage. In both cases, downtimes are avoided, and productivity guaranteed.
With the access permission system PITreader, it is possible to implement numerous tasks relating to access permissions. Options range from a simple enable to replace a password to authentication for specific machine subfunctions, the safeguarding of safety gates through to a complex, hierarchical permission matrix and company-specific coding for additional tamper protection.
Particularly with the safety gate guarding that many machines require, the access permission system PITreader provides an additional safety aspect. It is possible to release a guard locking device only after authentication. The same applies to control units such as the pushbutton unit PITgatebox. With the integrated access permission system PITreader, this represents the ideal solution for authentication and operation in one device and guarantees that only authorized staff can execute commands such as stop, unlock, lock or reset on the plant.
Discover more about the individual safety gate solution
Data protection and network security
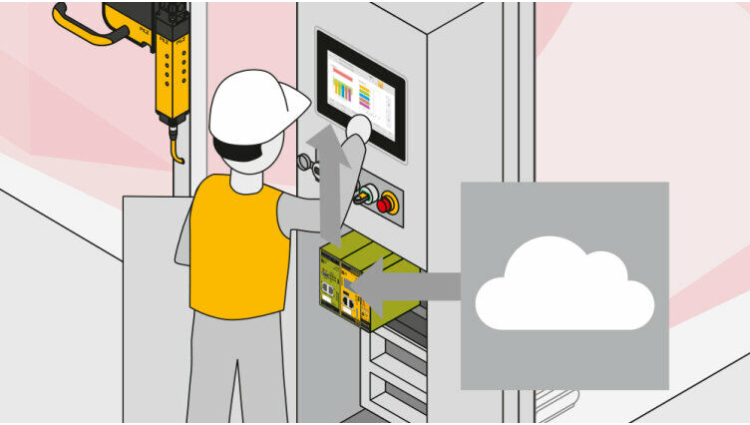
Data protection and network security is becoming ever more relevant around industrial installations. A safety concept needs to consider aspects of both safety and security. Only a holistic approach can effectively prevent vulnerabilities. The best safety gate protection is worthless if your data, know-how and operations are not sufficiently secured against unauthorized access and an external attacker penetrates your control network or tampers with the control system.
The industrial SecurityBridge firewall protects the data flow to your PILZ controller from “external” threats, such as hacker attacks for example, thus protecting it from tampering. The firewall monitors the data traffic between the PC and controller and reports any unauthorized changes to the control project. That way it provides effective protection against network-based attacks and unauthorized access.
The activatable USB interface PIT oe USB protects against hazards from “within”, whether due to carelessness or intent. In conjunction with the access permission system PITreader and authentication via personal RFID transponder, the USB port is only activated for authorized persons and is only enabled for such persons to use USB devices on your machines. As such you have additional security when, for example, you need to operate input devices such as a mouse or keypad or need to import or export data via a USB device.
More details about the industrial firewall SecurityBridge
Further information about industrial security
Overview of other application examples
Simple recipe management
Different keys can be used to easily initiate a quick change between different manufacturing products. Technical settings on plant and machinery can also be adapted using preconfigured keys. This enables a seamless switchover of production batches, for example. This directly contributes to reducing setup times while at the same time increasing the quality of production.
Individualization for users
On their key, all users are enabled for the exact functions for which they are qualified and authorized. So, machine and plant operators can have clear, language-dependent operator menus available on the HMI. They only see the functions that are enabled for them. This increases identification with the process considerably and significantly reduces the error rate. The omission of non-personalized, well-known passwords saves time when logging in and increases productivity.
Company-specific coding
A special signature is generated in the PITreader by inputting an identifier in the integrated web server. This tamper-proof signature is stored in the internal security chip from MIFARE. As a result, it is possible to create company or plantspecific PITreaders, for example. All transponder keys that are not taught in can be blocked from the outset. Only taught transponders that the system recognizes have a basic access right to coded PITreaders
Block list for keys
Transponder keys can be added to a so-called block list. Keys on the block list stored in the PITreader are blocked for further use. This measure protects against unauthorized access, if a key was lost or someone did not return the transponder key, for example. This always guarantees full control over permission management. Unwanted access is avoided, and tampering attempts are prevented. Plant and machinery are efficiently protected.
Key actions are logged (audit trail)
The logging function integrated in the PITreader enables personalized recording of access to plant or machinery, while processes can be recorded in full. The non-modifiable, tamper-proof documentation of all transponder actions enables simple traceability in the event of misuse, accidents, failures or plant diagnostics. Actions can be clearly assigned to a user. Lifetimes can also be deduced thanks to performance indicators. If logging is not allowed for operational reasons, the function can be switched off or only anonymous key actions can be logged.
Temporary permission
Access can be limited at any time! Access can only be achieved within the valid ranges provided. It is possible to store a start or end date. The validity can be based on a start time, end time or time period. Transponder keys have no permission outside of the period of validity and are blocked on the PITreader. The function can be used for processes in which certificates expire or annual checks are performed, for example. The temporary permission can also be used for rental and leasing arrangements. Individual days can also be enabled as the shortest unit for certain service activities.
Further information:
Identification and Access Management
How do you master the subjects of employee protection, liability protection, productivity and data protection? With Identification and Access Management or IAM you will find the right solution and get safety and security in one system.
Operating mode selection and access permission system form PITmode
PITMode combines safety and security functions in one system. The devices enable functionally safe operating mode selection and the control of access permission
Related Video
PITmode fusion – Your New Operating Mode Selection and Access Permission System